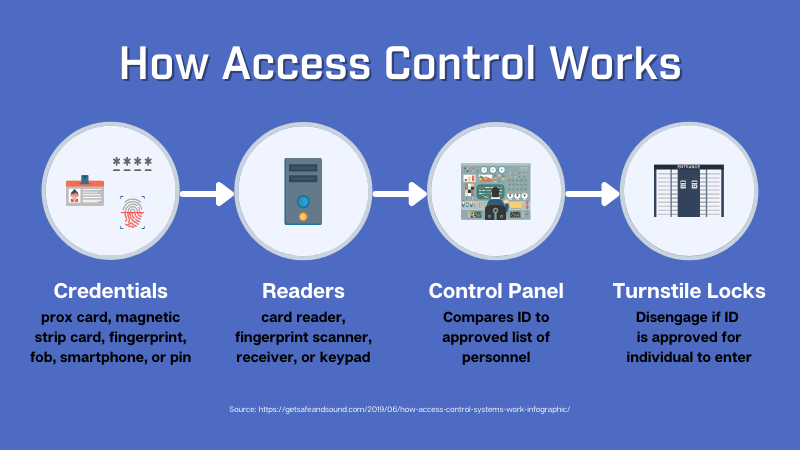
If you are unfamiliar with access control, this article will explain how this security system works. The key components of access control are authentication and authorization. Authentication like Biometric scanners identifies the body’s unique characteristics. It specifically requires physical identifiers, which the user always has with them. These identifiers verify a user’s identity and allow access to a secured area. Check out this article to know more about how access control works.
Authentication
Authentication in access control allows you to grant or deny users access to specific systems or resources, such as corporate networks, machines, and servers. By verifying an individual’s identity, access control can prevent unauthorized users. Depending on the access control, you can choose a single factor or multi-factor authentication. Multi-factor authentication uses several factors to verify an individual’s identity, such as their biometric fingerprint or location. Authentication in access control can also be accomplished using a simplified single-sign-on system (SSO) that grants users access to multiple systems using a single set of login credentials.
Authentication in access control involves rigorous implementation. The system verifies an individual’s identity during the process, which determines whether that person is authorized to view or edit a resource. The idea of least privilege, which limits the rights of employees and other individuals to the bare minimum, is one way of implementing authorization. In addition, the system can provide access and prohibit unauthorized individuals from accessing sensitive information once the appropriate degree of access has been established.
Security gaps
There are numerous gaps in access control and authorization. Authorization refers to providing the proper data access to an individual based on their identity. In many cases, an individual can be let go from their job. However, the asset remains connected to the organization’s internal infrastructure and is therefore still in the hands of a former employee. Such a situation can create significant problems for an organization. Therefore, authorization is critical to ensure the security of the company’s information.
In the past, an access control breach meant a criminal could gain access to a building and steal property. Today, bad actors exploit this vulnerability to hack into networks, infiltrate systems, and install malware to access sensitive information. Earlier, security measures meant having a separate network for access control. This approach had its problems and was difficult to hack. However, advances in technology have made it more vulnerable to cyberattacks.
Cost
Several factors will determine the cost of access control systems. These include the type of security required, the volume of purchases, and the ease of use. Some plans are cheaper than others, but some feature complex functionality. Portability is another factor, with portable cards resembling credit cards. Each user carries an access card. Larger companies may use a cloud-based service that lowers the cost of materials. Lastly, the amount of support you need can affect the price.
Some access control systems are highly customizable and affordable for small businesses. You can choose to start small by implementing only the most important access points and then add cameras and readers as your budget allows. Additionally, bringing access control online can streamline the management of employees. Instead of having employees carry keys, managers and owners can easily remove an employee’s credentials with a mouse click. Streamlining the employee management process will save both time and money.
Installation
Installing access control systems has its own set of challenges:
- It is essential to ensure that the wiring of the panels can reach the controlled doors within the distances of the credential readers selected.
- The panels must be installed to operate without a host computer, thereby decentralizing the control process.
- The controller panels must be placed to make programmed access decisions without a host computer.
Lastly, the installation process of an access control system involves the wiring of the interface. Following the installation manual or approved wiring drawing for a single reader, interfaces are important. The controller must be fitted within the enclosure when the wiring is completed. The dual reader interface and the Request to Exit button should be installed on the secure side of the door. It’s crucial to follow the manufacturer’s recommended layout when using a single reader interface. Once these are installed, make sure to mark the mounting plate’s location and height.